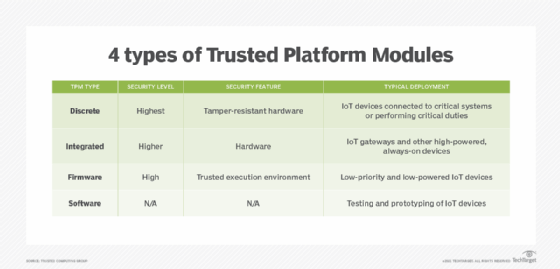
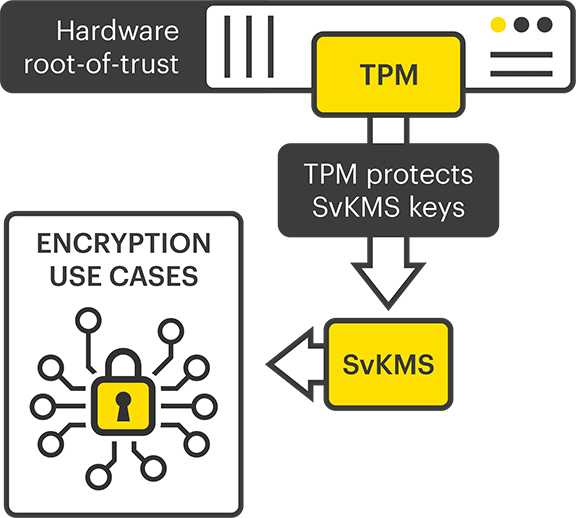
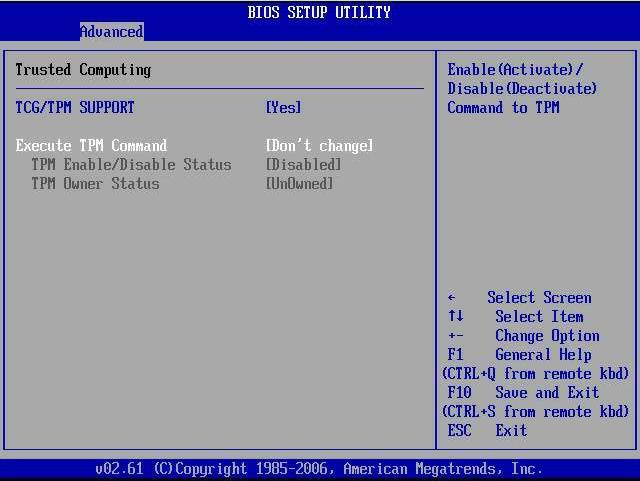
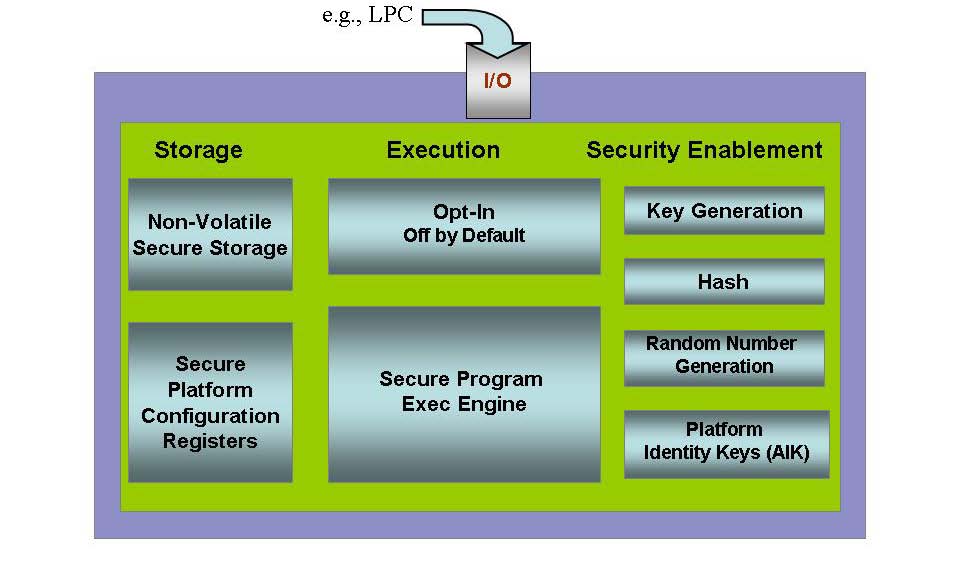
Trusted Computing Platforms: TPM2.0 in Context: Proudler, Graeme, Chen, Liqun, Dalton, Chris: 9783319087436: Amazon.com: Books

European Centre for IT-Security ( eurobits ) 1 European Multilateral Secure Computing Base Open Trusted Computing for You and | Semantic Scholar

CISSP PRACTICE QUESTIONS – 20210125 by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
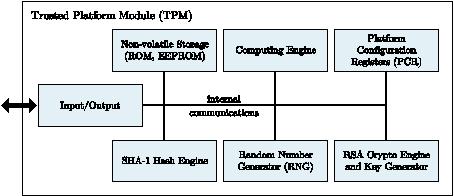
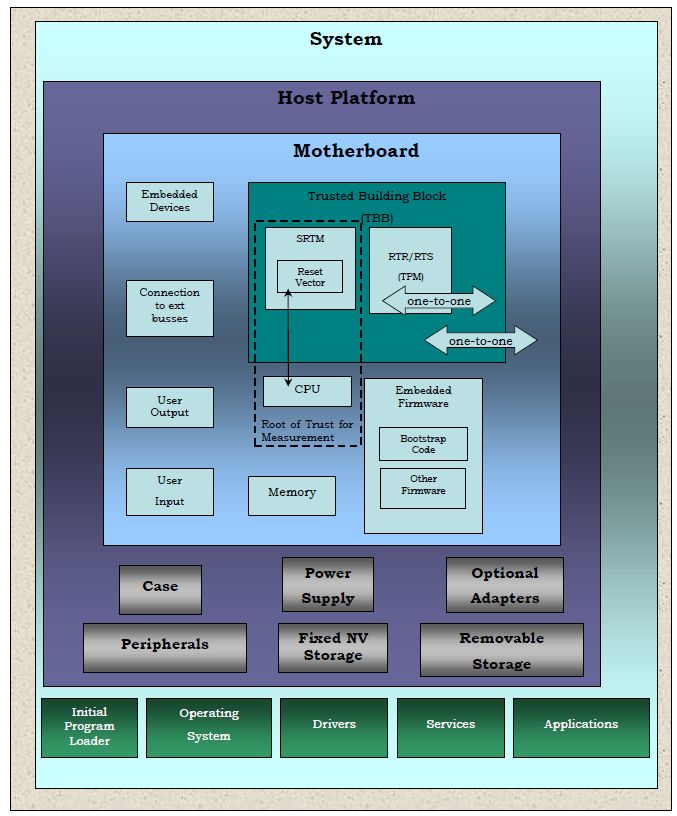
D3.9: Study on the Impact of Trusted Computing on Identity and Identity Management: Future of IDentity in the Information Society
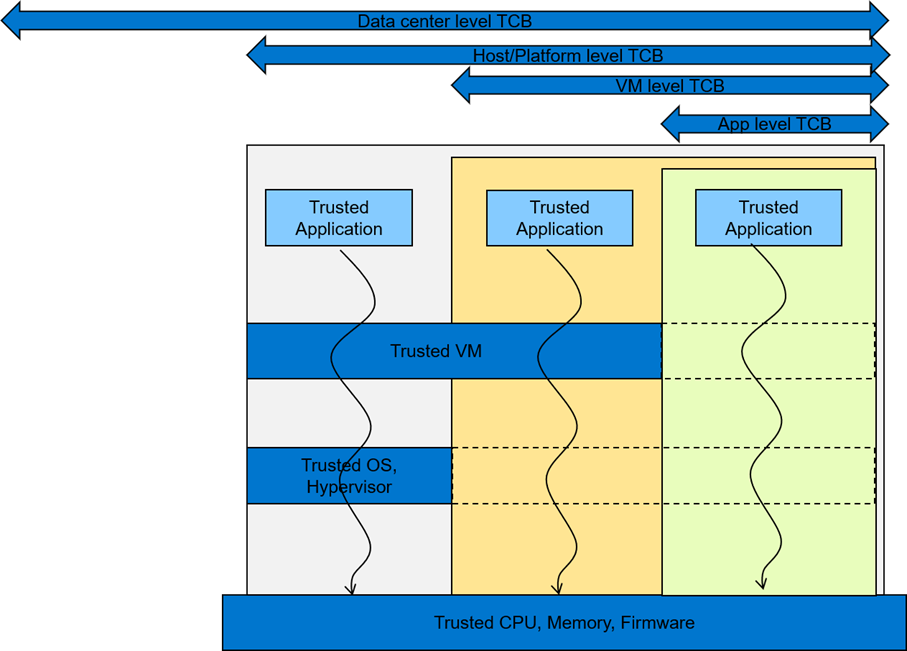
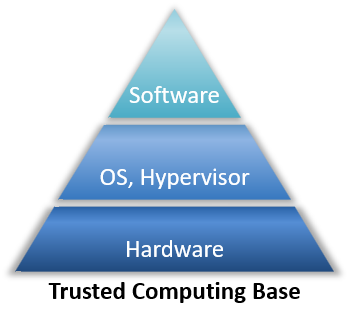
Understanding Confidential Computing with Trusted Execution Environments and Trusted Computing Base models | Dell Technologies Info Hub